Gateway and Certificate Authority troubleshooting
The table below provides information for problems with managing your Gateway configuration and Certificate Authority.
Note: You will need to change the file permissions of the logs generated from your Identity as a Service gateway before sending them to the Entrust support team. Enter Chmod 777 /path/<log_file_location> to change the file permissions.
Table: Troubleshooting scenarios
|
Problem |
Solution |
|
The gateway is not operating properly and the source of the problem cannot be identified. |
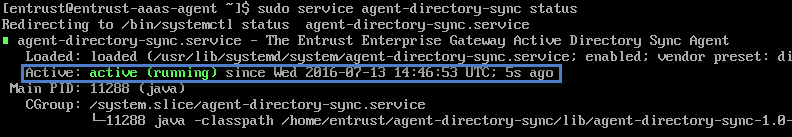
If you cannot identify the cause of your Gateway error, retrieve the Gateway logs associated to your Identity as a Service Gateway and contact the Entrust support team. Power on your virtual machine. Log in to your account using the username and password that you created when you Installed the Enterprise Gateway. Enter sudo service agent-directory-sync status. The Active Directory (AD) sync agent appears.
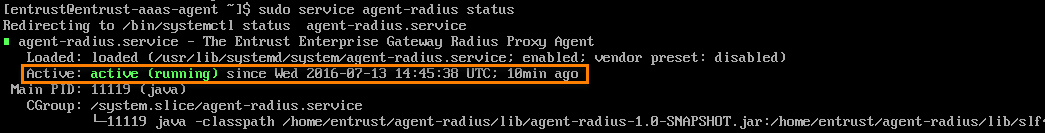
Validate that the directory sync is running by confirming that Active: active (running) appears. Enter sudo service agent-radius status to display the status of the RADIUS agent.
Validate that the RADIUS agent is running by confirming that Active: active (running) appears. Record whether the RADIUS agent and AD sync agents are active or inactive. You will need to include this information in your email to the Entrust support team. Enter sudo journalctl -u agent-radius > agent-radius-log.txt. This saves the RADIUS log to a separate log file entitled agent-radius-log.txt. Enter sudo journalctl -u agent-directory-sync > agent-directory-sync-log.txt. This saves the directory sync log to a separate log file entitled agent-directory-sync-log.txt. Find and record the directory path and file names of the logs you have saved. You need a member of your IT department to locate those logs in order to send them to the Entrust support team. Enter pwd to display the directory path you are located in. Record the directory path. Contact your IT department to pull up both log files (which they can access through an SFTP session). Provide your IT member with the directory path you identified in step 12, and the log file names agent-radius-log.txt and agent-directory-sync-log.txt . Ask your IT member to locate and send the log files to support@entrust.com in an email that identifies the problem and indicates whether one or both agents are active or inactive. |
|
The Reset Password option for AD synchronized users does not work even after enabling SSL on the IDaaS directory setting for AD Connector. |
Add the following registry key under HKEY_LOCAL_MACHINE\SOFTWARE\IDaaS Ad Connector: Name: PasswordChangeRequireTLS Type: REG_DWORD |
|
IDaaS AD Sync Error: email_delivery_error "Error sending email" Problem: Users are not being added to IDaaS after Directory synchronization. The following error appears in Splunk: Error occurred while batch updating user xxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxx in directory xxxxxx-xxxx-xxxx-xxxx-xxxxxxxx. java.lang.RuntimeException: class com.entrust.sbp.common.api.error.ServiceException: {"errorCode":"email_delivery_error","errorMessage":"Error sending email.","parameters":null} |
Workaround: Change the Mail server from Custom Mail Server to Built-in Mail Server (go to IDaaS > Menu > Configuration > Mail Server). Fix: Check your Custom Mail Server configuration and correct the email address. |
|
Reset password by user gives Access to the application denied error. |
Check the settings under IDaaS > Menu > Policies > General and set the Lockout Mode to Authenticator. |
|
LDAP error code 19 in IDaaS Gateway password agent logs |
This exception is generated by LDAP during the process of resetting the Active Directory password on the IDaaS user portal. This exception appears if the user fails to reset the password due to any of the following reasons: The new password does not meet the expected length. The new password does not meet the expected complexity. The new password does not meet the history requirement of the domain. End users must satisfy all the requirements listed in the user portal during the password reset process. |
|
HTTPS Decryption (MITM Proxy) was enabled unintentionally for the Gateway, causing all requests to IDaaS from the IDaaS Gateway to fail. For HTTPS Decryption (MITM Proxy), the new root CA needs to be imported into the IDaaS Gateway. The following error appears when trying to register the gateway: Error registering gateway: PKIX path building failed... unable to find valid certification path to requested target executing POST... |
Add a private trusted CA to the IDaaS Gateway. Workaround: Use the following command on the IDaaS Gateway Cent OS: Install the ca-certificates package: yum install ca-certificates Enable the dynamic CA configuration feature: update-ca-trust force-enable Add it as a new file to /etc/pki/ca-trust/source/anchors/: cp foo.crt /etc/pki/ca-trust/source/anchors/ Use command: update-ca-trust extract |
|
IDaaS Gateway rolled back to an old DNS value after a Gateway upgrade. |
Log in to the Gateway GUI at https://<ipaddress>:9090 and configure the DNS servers there instead of manually editing the /etc/resolv.conf file on the Gateway. |
|
Error message "Job for network.service failed because the control process exited with error code. See 'systemctl status network.service' and journalctl -xe" for details. Child returned l" appears after entering setup_dhcp during configuration. |
There is no address available from DHCP for the gateway. To resolve this issue, examine your virtualization environment to confirm the DHCP server has addresses available. Add addresses to your DHCP if there are none available, and retry the operation again. |
|
New password entered into Gateway agent during initial configuration is not accepted. |
Confirm that the password you are attempting to enter does not violate any of the following restrictions: The password is not similar to the old one. The password is not a word found in the dictionary. The password entered the first and second times match. The password contains at least 8 characters. If your password does not violate these constraints and you still cannot create a new password, contact support@entrust.com for assistance. |
|
Issues with running setup_appliance |
Analyze the error logs under /opt/entrust/gateway/enterprise_gateway_startup.log If required, contact support@entrust.com for assistance. |
|
Gateway is not starting up properly |
Analyze the error logs under /opt/entrust/gateway/enterprise_gateway_initialization.log If required, contact support@entrust.com for assistance. |
|
How do I access the Entrust Identity Enterprise Gateway agent logs? |
Enter sudo journalctl -u agent-idg -f into the Gateway command prompt. |
|
How do I access the Entrust Identity Enterprise Gateway agent logs within a specific time period? |
Enter sudo journalctl -u agent-idg --since "<yyyy-mm-dd hh:mm>" into the Gateway command prompt. |
|
How do I access the Entrust Identity Enterprise Gateway proxy startup/configuration logs? |
Enter "sudo less /opt/entrust/gateway/enterprise-gateway-initialization.log" into the Gateway command prompt. |
|
Microsoft CA Proxy certificates cannot be verified. |
To get the KRA back into a working state (valid), in the Microsoft CA publish a new CRL by right-clicking the Revoked Certificates node and then click All Tasks / Publish. |
|
How do I access the Password Agent and CA Gateway logs? |
Enter sudo journalctl -u agent-password -f into the Gateway command prompt. Enter sudo journalctl -u cagw -f into the Gateway command prompt. |
|
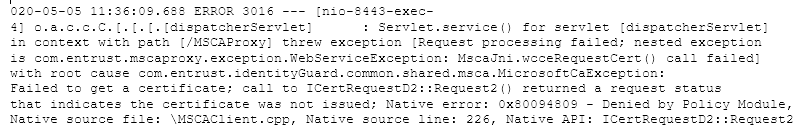
I received an invalid issuance policy error. |
Sample error: Failed to get a certificate; call to ICertRequestD2::Request2() returned a request status that indicates the certificate was not issued; Native error: 0x800b0113 - Error Constructing or Publishing Certificate Invalid Issuance Policies: 2.16.840.1.101.3.2.1.3.13, Native source file: \MSCAClient.cpp, Native source line: 226, Native API: ICertRequestD2::Request2 This type of error occurs if your CA does not support the id-fpki-common-authentication or the id-fpki-common-cardAuth issuance policy. |
|
Encoding fails with a Microsoft CA |
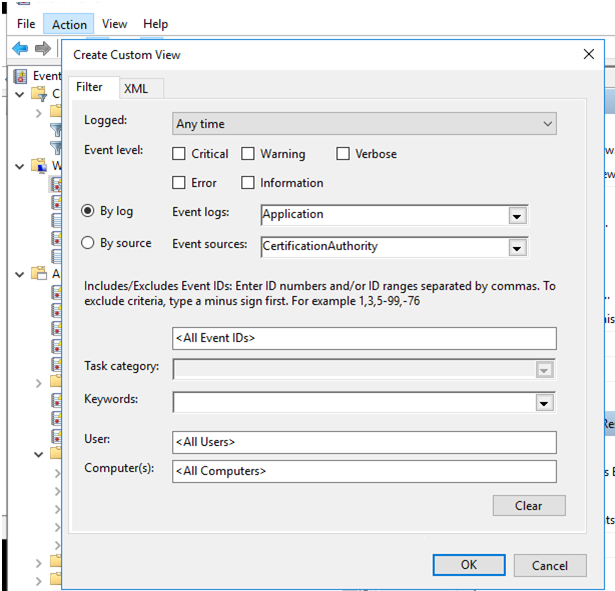
Enter sudo journalctl -u cagw -f into the Gateway command prompt. Check additional information and logs here: MS CA Proxy service log MS CA Service events Note: The proxy logs are found in the location where you installed the MS CA Proxy. You can view Certificate Authority Service events by setting up a custom view as follows: Open the Event Viewer and click Action. The Create Custom View dialog box appears.
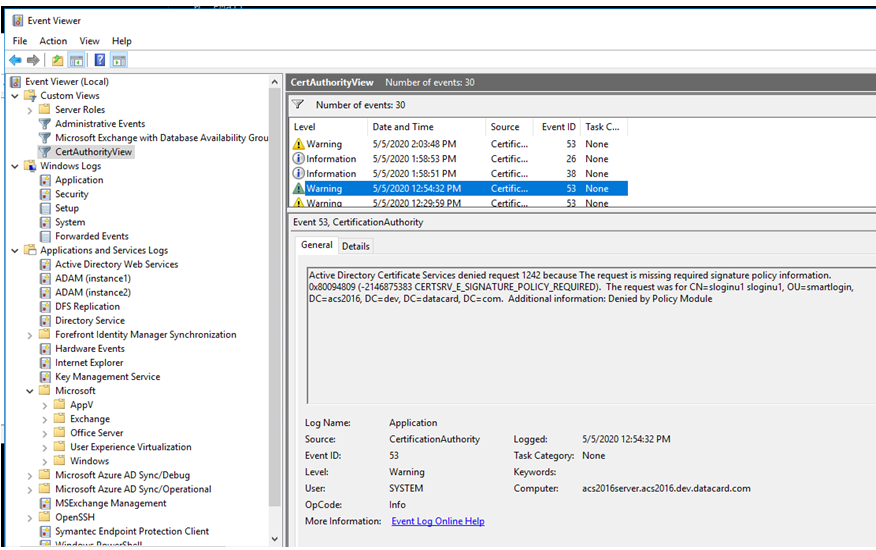
From the Event Logs drop-down list, select Application. From the Event Sources drop-down list, select CertificationAuthority. The following is an example of a certificate request error:
Create PIV - PIV Authentication certificate template Create the Digital Signature certificate template Create the PIV - Key Management template Check Create the PIV - Content Signer (device) certificate template to ensure that you configured Authorized Signatures is set to 1 and that Publish to AD is not selected. If this occurs, you will get this System Event on the Certificate Authority:
:And the corresponding error in the Microsoft CA proxy log
|
|
Authentication fails certificate validation with a Microsoft CA |
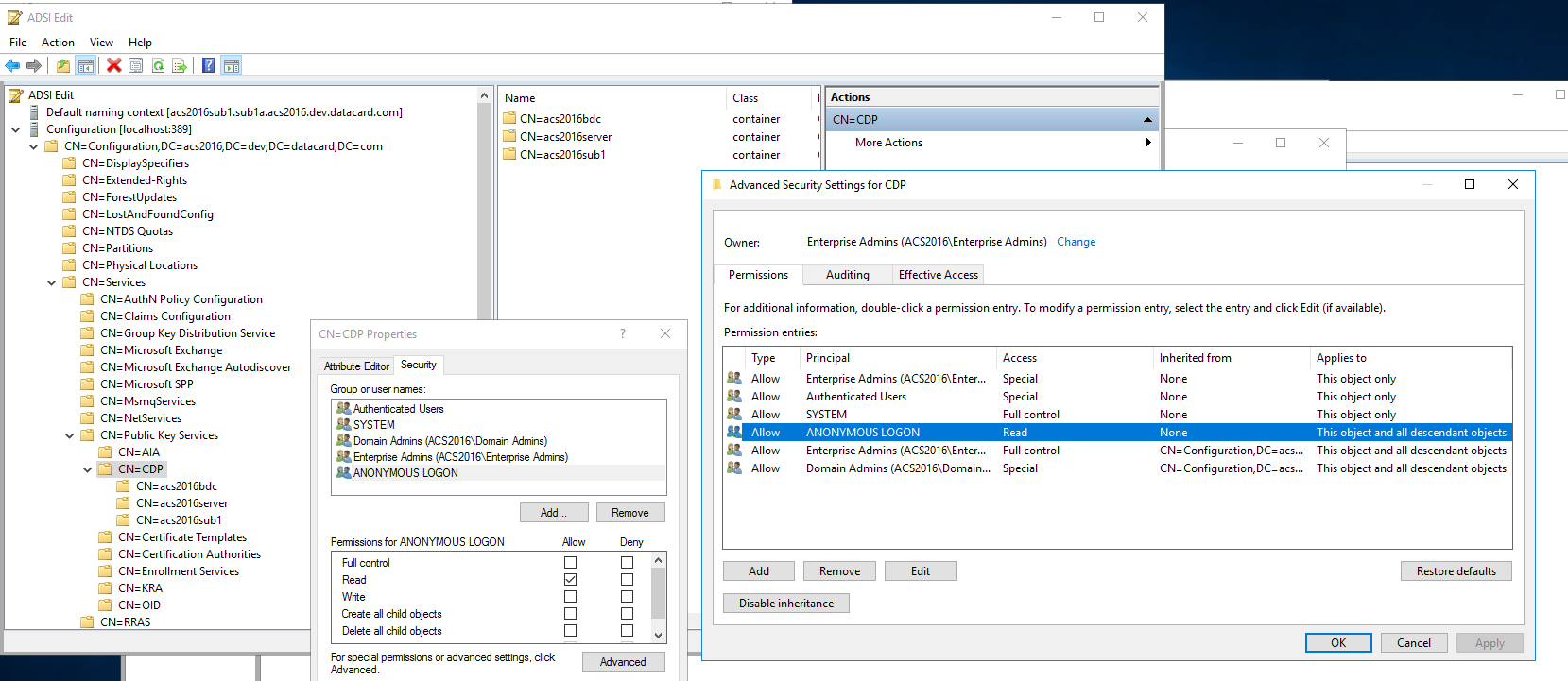
ldap CRLs and AIA data are only supported in an anonymous manner over ldap (non-ssl). In addition to CRL information being present in user certificates, any intermediate CA certificate issuing these certificates must also have this CRL information present in order for the intermediate CA certificates to be validated. The following link provides more information if CRLs are not currently available in this manner: https://social.technet.microsoft.com/wiki/contents/articles/51431.adcs-change-your-default-ldap-based-cdp-and-allow-anonymous-access-to-the-new-cdp.aspx. These updates apply to the CDP and AIA modes. Additionally, read permissions on the CDP node and the AIA node should also be granted to descendant objects. See the following image for an example of how this is done for the CDP node. The same would apply for the AIA node.
|