Create the PIV - PIV Authentication certificate template
Use this procedure to create the PIV-PIV Authentication certificate template.
It is important to create this template first because you will create the other PIV templates described in this section by duplicating this template. Some settings in this template are common to all the PIV templates.
On the Microsoft CA machine, go to Start > Windows Administrative Tools > Certification Authority.
Click your certification authority to expand the root folder.
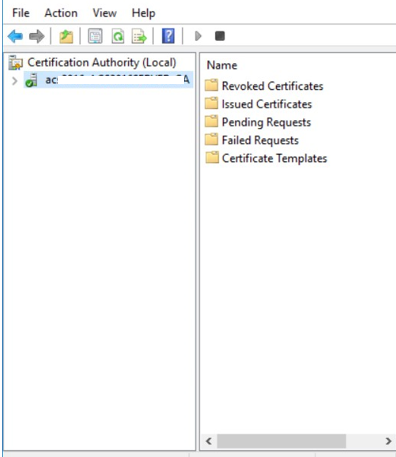
Right-click Certificate Templates, and then select Manage. The Certificate Templates Console appears.
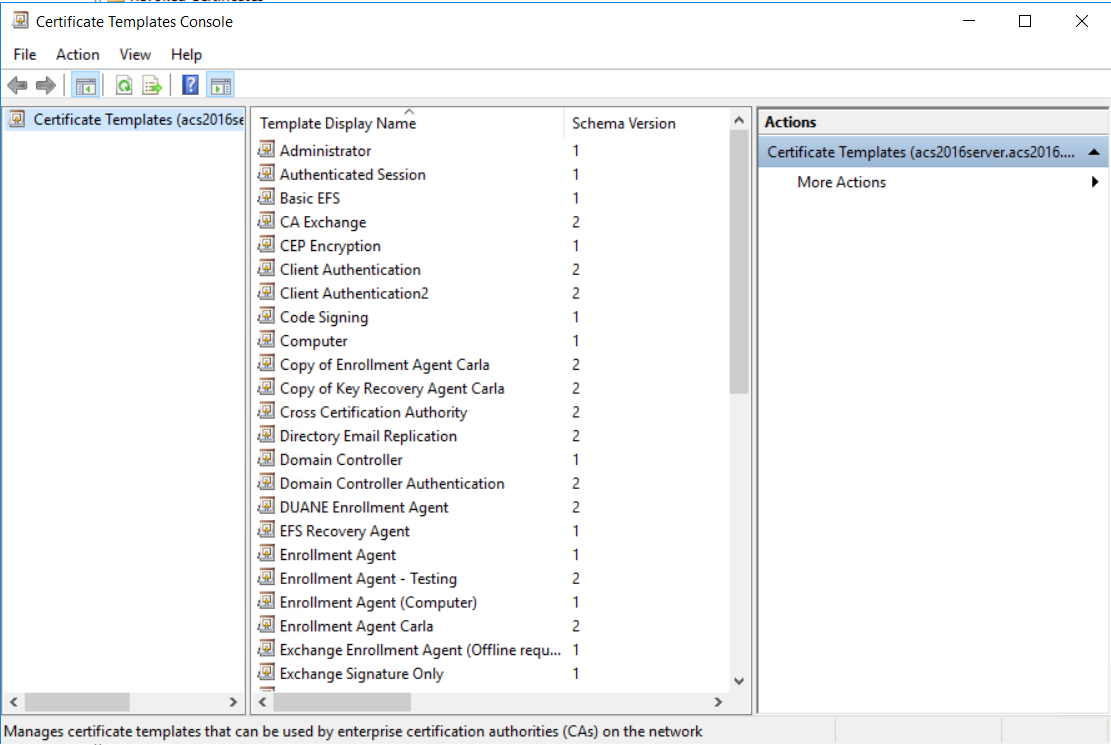
Scroll the template list, right-click the User template and select Duplicate Template. The Properties of New Template dialog box appears.
In the Compatibility Settings, select the following:
From the Certificate Authority drop-down list, select
Windows Server 2012R2 if you are running on a 2012R2 server
-or-
Windows Server 2016 if you are running on Windows Server 2016 or later
From the Certificate Recipient drop-down list, select
Windows 8.1/Windows Server 2012R2 if you are running on a 2012R2 server
-or-
Windows 10/Windows Server 2016 if you are running on Windows Server 2016 or later
Click OK.
(Optional) If the Show resulting changes check box is selected a message lists the options that will be added with you choice. Click OK to dismiss the message.
Click the General tab.
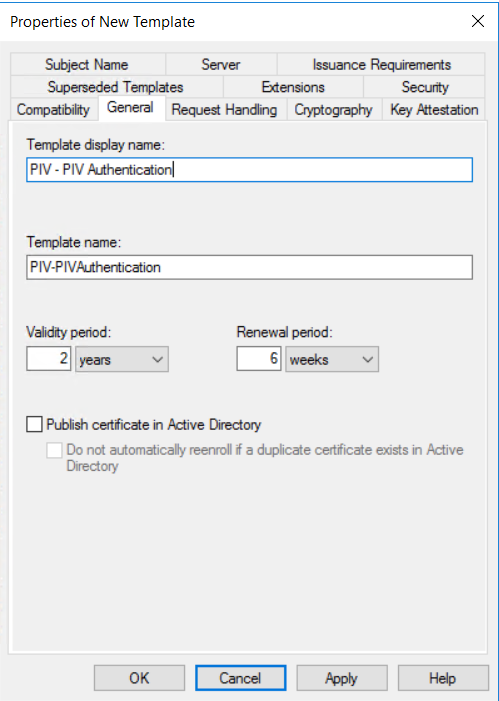
Configure the following settings:
In the Template display name field, enter PIV - PIV Authentication. The Template name field is filled in automatically with the template display name (with no spaces).
Optional. Select Publish certificate in Active Directory.
Click the Request Handling tab.
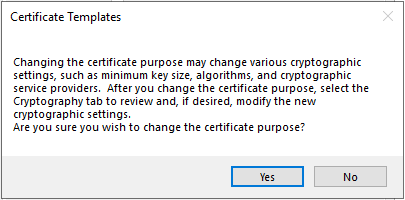
From the Purpose drop-down list, select Signature and smartcard logon.
When asked to confirm the change, click Yes.
Click the Cryptography tab, and configure the following:
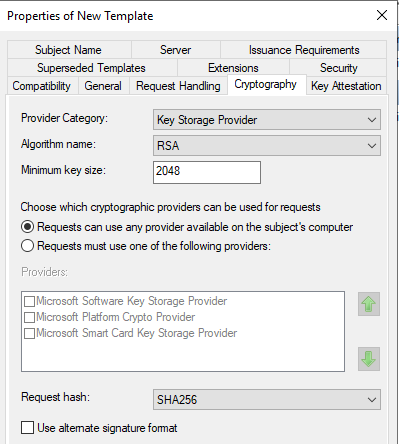
From the Provider Category drop-down list, select Key Storage Provider.
From the Algorithm name drop-down list, select RSA.
Set the Minimum key size to 2048.
From the Request hash drop-down list, select SHA256.
Click the Security tab and under Permissions for Authenticated Users reduce the permissions to no more than Read.
Add the <domain_user> and select Read and Enroll.
For all other users and groups, review the permissions and ensure that they have the desired access policy.
Click the Subject Name tab, configure the following settings:
Select Supply in the request and click OK to confirm the changes. In this case, security is maintained because only an administrator and the <domain_user> can request certificates associated with this template.
Click the Extensions tab.
Select Application Policies, and then click Edit. The Edit Application Policies Extension dialog box appears.

Add two new policies: Any Purpose and Smart Card Logon.
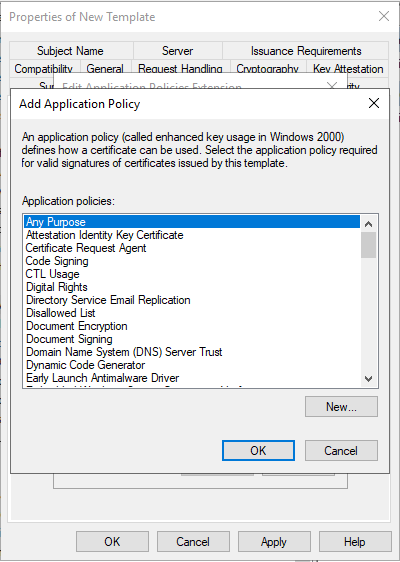
On the Edit Application Policies Extension dialog box, click Add. The Add Application Policy dialog box appears.
Under Application Policies dialog box, select Any Purpose, and then click OK.
Click Add.
From the Application Policies list, select Smart Card Logon and click OK.
On the Edit Application Policies Extension dialog box, remove the application policies that are not required.
Select Encrypting File System and click Remove.
Select Secure Email and click Remove.
The resulting list of application policies should have Any Purpose, Client Authentication, and Smart Card Logon.
Click OK to close the dialog box.
In the Extensions tab, select Issuance Policies and then click Edit. The Edit Issuance Policies dialog box appears.
Attention: You can add PIV policies as required by your organization. The id-fpki-common-authentication issuance policy provided in the following steps is used by the U.S. Federal Government. Organizations outside of the U.S. Federal Government may not be able to issue or use these issuance policies. You should test your CA policy configuration with the applications they intend to use to ensure compatibility. If your application does not support the issuance policy, then you should not configure it.
On the Edit Issuance Policies dialog box, do the following:
Click Add. The Add Issuance Policy dialog box appears.
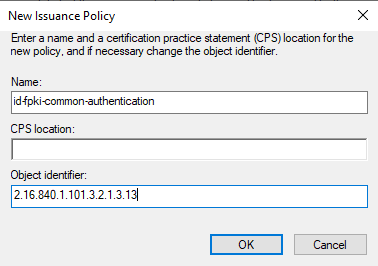
Click New. The New Issuance Policy dialog box appears.
In the Name field, enter id-fpki-common-authentication
Leave CPS location empty.
In the Object Identifier field, enter 2.16.840.1.101.3.2.1.3.13
Click OK to create the new extension policy.
If you chose to Publish to Active Directory, do the following:
Click the Issuance Requirements tab.
Select The number of authorized signatures and enter 1 in the text box.
From the Policy type required in signature drop-down list, select Application policy.
From the Application policy drop-down list, select Certificate Request Agent.
Click OK to close the open dialog boxes to return to the Certificate Templates Console.
The PIV - PIV Authentication certificate template is added to the list of templates.