Manage user certificate authenticators
A User Certificate can be used for the following:
First-factor authentication for User Login to enable passwordless log in to the User Portal, SAML or OIDC and OAuth applications.
Second-factor authentication for User Login to the User Portal, SAML or OIDC and OAuth applications.
Limitations
The following are limitations of user certificate authenticators:
In addition to the IDaaS portal domain customer.region.trustedauth.com, the network must also allow the SSL service domain customer.region.ssl.trustedauth.com.
RADIUS applications and Entrust Identity Enterprise integrations do not support Passkey/FIDO2 authentication.
User certificate authentication must be enabled by an administrator for the application.
Requirements
The following requirements must be met to use a user certificate authenticator:
Users must have the following when authentication with certificate issued by trusted CAs:
A user certificate with required certificate components configured by the matching rules.
A private key for the user certificate.
A user attribute that matches the user to the user certificate.
Users must have the following when authentication with smart credentials issued by IDaaS:
A IDaaS issued smart credential. It can be either mobile smart credential or physical smart credential.
The smart credential is connected to the computer and the smartcard reader is ready.
How it works
When enabled for passwordless user login, the user sees a Certificate button on the login screen. They do not enter their user ID and password. They simply click the Certificate button and a Certificate prompt appears for them to select the certificate used to sign in. The certificates available in the prompt is filtered by the trusted CAs and issuing CAs. If a unique user is identified by the provided user certificate, the user is logged into the application as the derived user.
When enabled for second-factor authentication, the user enters their user ID and password. They then click the User Certificate Authentication button for second-factor authentication. A Certificate prompt appears for them to select the certificate used to sign in. If the same user is identified by the provided user certificate, the user is logged into the application.
How to set up User Certificate authentication
To use user certificate from the smart credential from IDaaS, no additional CA configuration is required. To use user certificate issued by external CA, import the Trusted CA that issues the user certificate. See Configure a Trusted CA and select the Use as a User Certificate CA checkbox.
If using the user certificate issued by external CA, configure the policy for User Certificate Authentication. See Modify user certificate authenticator settings. The user certificates from smart credentials don’t use the user certificate authenticator settings to find the user.
Ensure that users have the required certificate matching attribute populated in their user profile. See Modify user certificate authenticator settings and Edit, delete, unlock, and disable users.
Create an authentication flow to allow User Certificate to be used for either first-factor (passwordless) or second-factor authentication. See Create authentication flows.
Create a resource rule for the application. See Create resource rules.
Select user certificate login under Enable Authentication Flow for the application. See Integrate SAML applications, Integrate OIDC and OAuth Cloud applications, and Edit and delete applications.
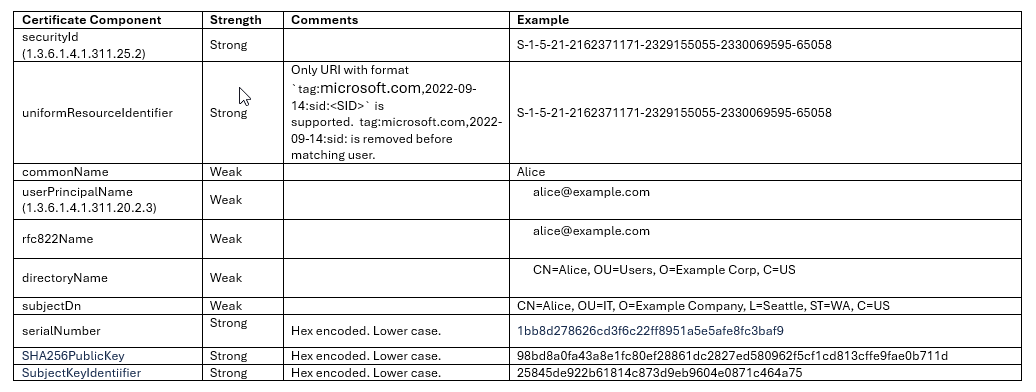
Supported certificate components
The following table summarizes supported certificate components.
User matching process
When using only weak identifiers, all weak identifiers must be included and must all match rules match the target user. When a certificate has multiple weak Certificate Components, such as CNs, UPNs, rfc822Names, it is treated as though the certificate does not have that component.
If any strong identifiers are configured, weak identifier matching rules are ignored. Strong identifier matching rules are evaluated sequentially; only the first rule with the lowest order number as strong identifiers should be unique.