Create authentication flows
An authentication flow determines how a user authenticates. IDaaS supports the following authentication flows:
User Login—The user enters their user ID and is prompted to authenticate using any of the IDaaS authenticators.
Smart Login—The user interacts with an Entrust Identity Smart Credential to authenticate. The user does not enter their userID because authentication involves a passwordless authentication flow. The user ID is obtained from the Smart Credential.
Smart Login is available only if the account has been enabled to allow Smart Login. Smart Login can be used to authenticate to the Identity as a Service Admin Portal, User Portal, OIDC, and SAML applications integrated with Identity as a Service.
Note: Entrust recommends that User Login flow should also be enabled when Smart Login is selected in an authentication flow.
Passkey—The user authenticates with a FIDO2/Passkey token. The user does not enter their user ID because authentication involves a passwordless authentication flow. The user ID is obtained from the FIDO2/Passkey token.
Identity Provider—The user is forwarded to an external SAML or OIDC Identity Provider to authenticate. The user ID is provided by the Identity Provider.
User Certificate—TThe user authenticates with a user certificate. The user does not enter their user ID because authentication involves a passwordless authentication flow. The user ID is obtained from the user certificate.
When you create a resource rule, you need to select an authentication flow for the rule. You can select to use a system authentication flow or create a custom flow. IDaaS has the following pre-configured System Authentication Flows:
Default Second-Factor OnlyDefault Second-Factor Only
Domain-Based IDP OnlyDomain-Based IDP Only
Domain-Based IDP or User LoginDomain-Based IDP or User Login
External and Second FactorExternal and Second Factor
Password and Second FactorPassword and Second Factor
Password and Software/Hardware TokenPassword and Software/Hardware Token
Smart Login OnlySmart Login Only
Software/Hardware Token and Temporary Access CodeSoftware/Hardware Token and Temporary Access Code
Software/Hardware Token OnlySoftware/Hardware Token Only
User Certificate OnlyUser Certificate Only
If the authentication flow is not available for the required authentication method, clone a system authentication flow and then select the preferred second-factor authenticator.
For example, to allow Magic Links for authentication, do the following:
Clone the Default Second Factor Only system authentication flow.
Select Magic Link as a second-factor authenticator.
Manage Authentication Flows
View authentication flowsView authentication flows
View authentication flows
Click ![]() > Security > Authentication Flows. The Authentication Flows page appears.
> Security > Authentication Flows. The Authentication Flows page appears.
Click ![]() next to the authentication flow to see the flowchart.
next to the authentication flow to see the flowchart.
Click OK to close the flow.
-or-
Click the name of the authentication flow (for example, Access Denied).
Click Cancel to return to the Authentication Flows list.
Clone an authentication flowClone an authentication flow
When you clone an authentication flow, you can do the following:
Give it a new name.
Change the Login Flows.
Select the First Factor for User Login flow.
Select and reorder the Second Factor authenticators for the Login Flow.
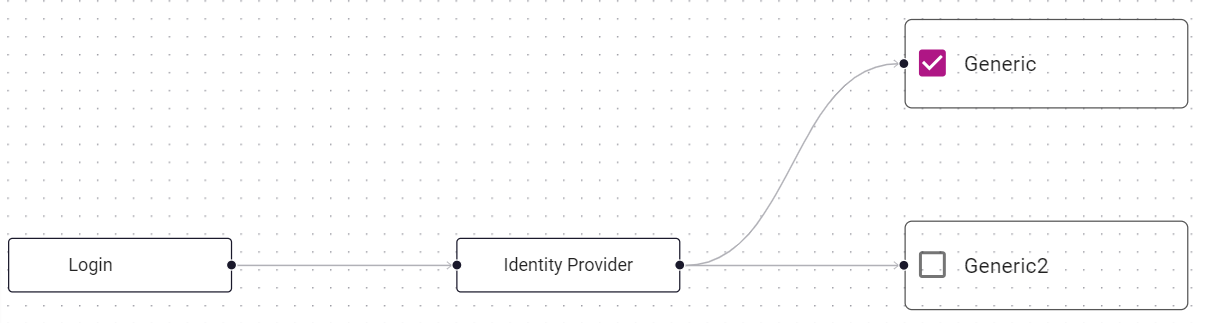
Note: If you enable Identity Provider as a Login Flow, select the Identity Providers the user can access through the authentication flow as shown in the following figure.
Clone an authentication flow
Click ![]() > Security > Authentication Flows. The Authentication Flows page appears.
> Security > Authentication Flows. The Authentication Flows page appears.
Click ![]() next to the authentication flow you want to clone.
next to the authentication flow you want to clone.
By default the name appears labelled copy (for example, Password and Second Factor copy).
Edit the following, as required:
Enter a Name for the authentication flow.
Select the applicable Enable Login Flows.
User Certificate is a passwordless authentication option that allows a user to use a certificate to log in.
Smart Login and Passkey are authentication options that do not require the user ID to be entered first.
Identity Provider forwards the user to an external SAML or OIDC Identity Provider to authenticate, for example, Facebook. Identity Provider does not require the user ID to be entered first.
User Login requires the user to log in with their username and then respond to an authentication challenge presented by IDaaS.
If you enable Identity Provider as a Login Flow, complete the following:
Select the Identity Providers the user can access through the resource rule as shown in the following sample figure.
In this example, Generic requires access through the conditions of the resource rule. Generic2 cannot be used in this authentication flow.

If you want to require second-factor authentication to access an Identity Provider, select Enable Second Factor for Identity Provider.
Select the Second Factor authenticators that can be used for authentication.
Click and drag the selected Second Factors authenticators so that they are ordered from top to bottom in order of preference.
Note: If you want to configure different second-factor authentication requirements for various Identity Providers, you need to create a unique authentication flow for each one.
For example, if you want Generic to require grid or OTP for second-factor authentication but Generic2 to only require OTP, you need to create separate authentication flows and unique resource rules for each one—an authentication flow for Generic that requires grid and OTP and a second authentication flow for Generic2 that requires only OTP.
If you enable User Login flow, complete the following:
Select the First Factor from the drop-down list. The type of authenticator selected is the first type of authentication challenge a user must complete to access the application.
Select the Second Factor authenticators that can be used for authentication.
Click and drag the Second Factor authenticators so that they are ordered from top to bottom in order of preference.
These are the second-factor authentication methods required for authentication. The list of Second Factor authenticators available updates based on the type of first-factor authenticator selected.
Review the flow on the flowchart diagram.
Click Save.
Create a custom authentication flowCreate a custom authentication flow
Create an authentication flow
Click ![]() > Security > Authentication Flows. The Authentication Flows page appears.
> Security > Authentication Flows. The Authentication Flows page appears.
Under Custom Authentication Flows, click Add. The Authentication Flows page appears.
Note: You can additionally click and then edit the Custom authentication flow option provided on the page.
Enter a Name for the authentication flow.
Select the applicable Enable Login Flows.
User Certificate is a passwordless authentication option that allows a user to use a certificate to log in.
Smart Login and Passkey are authentication options that do not require the user ID to be entered first.
Identity Provider forwards the user to an external SAML or OIDC Identity Provider to authenticate, for example, Facebook. Identity Provider does not require the user ID to be entered first.
User Login requires the user to log in with their username and then respond to an authentication challenge presented by IDaaS.
If you enable Identity Provider as a Login Flow, complete the following:
Select Use Domain-Based Identity Providers to require users to log in using the Domain-based IDP only. If you select this option, only a domain-based IDP is available (see the figure below). Non-domain-based IDPs cannot be configured with domain-based IDPs in the same authentication flow.

If you do not enable Use Domain-Based Identity Providers, select the Identity Providers the user can access through the resource rule as shown in the following sample figure.
In this example, Generic requires access through the conditions of the resource rule. Generic2 cannot be used in this authentication flow.

If you want to require second-factor authentication in addition to accessing an Identity Provider, select Enable Second Factor for Identity Provider.
Select the Second Factor authenticators that can be used for authentication.
Click and drag the selected Second Factors authenticators so that they are ordered from top to bottom in order of preference.
Note: If you want to configure different second-factor authentication requirements for various Identity Providers, you need to create a unique authentication flow for each one.
For example, if you want Generic to require grid or OTP for second-factor authentication but Generic2 to only require OTP, you need to create separate authentication flows and unique resource rules for each one—an authentication flow for Generic that requires grid and OTP and a second authentication flow for Generic2 that requires only OTP.
If you enable User Login flow, complete the following:
Select the First Factor from the drop-down list. The type of authenticator selected is the first type of authentication challenge a user must complete to access the application.
Select the Second Factor authenticators that can be used for authentication.
Click and drag the Second Factor authenticators so that they are ordered from top to bottom in order of preference.
These are the second-factor authentication methods required for authentication. The list of Second Factor authenticators available updates based on the type of first-factor authenticator selected.
Review the flow on the flowchart diagram.
Click Save.
Edit an authentication flowEdit an authentication flow
Edit an authentication flow
Click ![]() > Security > Authentication Flows. The Authentication Flows page appears.
> Security > Authentication Flows. The Authentication Flows page appears.
Click the name of the authentication flow you want to edit. The Edit Authentication Flow page appears.
Edit the authentication flow as required using the instructions that follow.
Change the Name for the authentication flow.
Select the applicable Enable Login Flows.
User Certificate is a passwordless authentication option that allows a user to use a certificate to log in.
Smart Login and Passkey are authentication options that do not require the user ID to be entered first.
Identity Provider forwards the user to an external SAML or OIDC Identity Provider to authenticate, for example, Facebook. Identity Provider does not require the user ID to be entered first.
User Login requires the user to log in with their username and then respond to an authentication challenge presented by IDaaS.
If you enable Identity Provider as a Login Flow, complete the following:
Select the Identity Providers the user can access through the resource rule as shown in the following sample figure.
In this example, Generic requires access through the conditions of the resource rule. Generic2 cannot be used in this authentication flow.

If you want to require second-factor authentication in addition to accessing an Identity Provider, select Enable Second Factor for Identity Provider.
Select the Second Factor authenticators that can be used for authentication.
Click and drag the selected Second Factors authenticators so that they are ordered from top to bottom in order of preference.
Note: If you want to configure different second-factor authentication requirements for various Identity Providers, you need to create a unique authentication flow for each one.
For example, if you want Generic to require grid or OTP for second-factor authentication but Generic2 to only require OTP, you need to create separate authentication flows and unique resource rules for each one—an authentication flow for Generic that requires grid and OTP and a second authentication flow for Generic2 that requires only OTP.
If you enable User Login flow, complete the following:
Select the First Factor from the drop-down list. The type of authenticator selected is the first type of authentication challenge a user must complete to access the application.
Select the Second Factor authenticators that can be used for authentication.
Click and drag the Second Factor authenticators so that they are ordered from top to bottom in order of preference.
These are the second-factor authentication methods required for authentication. The list of Second Factor authenticators available updates based on the type of first-factor authenticator selected.
Review the flow on the flowchart diagram.
Click Save.
Delete an authentication flowDelete an authentication flow
Edit an authentication flow
Click ![]() > Security > Authentication Flows. The Authentication Flows page appears.
> Security > Authentication Flows. The Authentication Flows page appears.
Click  next to the authentication flow you want to delete. The Delete Authentication Flow confirmation prompt appears.
next to the authentication flow you want to delete. The Delete Authentication Flow confirmation prompt appears.
Click Delete.
Override OTP PolicyOverride OTP Policy
Use the Override OTP Policy feature to require a specific delivery method for the OTP regardless of the settings in the OTP authenticator policy. (see Manage One Time Passwords). If no OTP Override is selected, then the OTP delivery methods defined in the OTP policy are used.
To apply different Override OTP Policies to different applications, create an authentication for flow each application.
For example,
Application1 requires an OTP Override for Voice delivery. Create an Authentication flow to allow OTP for second-factor and configure the Override OTP Policy delivery method to Voice.
Application 2, requires an OTP Override for SMS delivery. Create an Authentication flow to allow OTP for second-factor and configure the Override OTP Policy delivery method to SMS.
Application 3 does not require any overrides. It uses the policies set for the OTP authenticator. Do not enable the Override OTP Policy in the Authentication Flow.
Clone the Authentication Flow to and ensure that OTP is selected as a second-factor authentication method.
Select Override OTP Policy.
Select the preferred OTP Delivery Methods.
If you select more than one OTP Delivery Method, drag and drop in order of preference.
Click Save.