Application help
The tables below provide troubleshooting information for problems those setting up and accessing Web applications could encounter. The information is organized into four tables:
Table 1: Add Salesforce application
Table 2: Add Google Workspace application
Table 3: Logging into Identity as a Service-configured applications
Table 4: Delete an application
Table 5: Configuring Entrust Identity Desktop for Microsoft Windows with Identity as a Service
Table 6: CORS log in error
Attention: For IDaaS clients, including the Enterprise Service Gateway, that connect to IDaaS, you must configure your firewall to allow connections to your IDaaS account. IDaaS uses HTTPS on port 443.
Table 1: Add Salesforce application
PROBLEM |
SOLUTION |
The administrator is unable to locate and download an Identity Provider certificate on the Identity as a Service administrator portal when configuring the SAML Single Sign-On (SSO) Settings. |
Contact support@entrust.com for assistance. |
The administrator is not being given the opportunity to create a domain name, and an existing domain name does not appear on the My Domain screen within the Salesforce account. |
Consult the Salesforce help documentation. Note: Open the link above in a new tab to access the Salesforce help documentation. |
The Register Domain button is not clickable within the Salesforce account. |
Confirm that the Confirm that you have checked off the Terms and Conditions check box. Contact the Salesforce support team for assistance. |
Entering the Identity as a Service account URL, followed by /api/saml/SAML2/metadata.xml (for example https://example.us.trustedauth.com/api/saml/SAML2/metadata.xml) does not lead the Web browser to generate the XML version of the desired Identity as a Service account. |
Confirm that there are no incorrect characters (upper or lower case) or spaces within the URL that you have entered. Contact support@entrust.com for assistance. |
There are no user attributes available for the Salesforce federation ID value to be added to a user's account. |
Create a new user attribute for your Salesforce Federation ID Attribute value. Assign that new user attribute value to any of the users that you want to have access to your Salesforce account. Assign the new user attribute as the Federation ID Attribute. |
The administrator does not know what to enter as the Single Sign-On URL when configuring Salesforce on Identity as a Service. |
Enter the Salesforce Login URL (which is also the Entity ID in your SAML Single Sign-On Settings) of your Salesforce account as the Single Sign-On URL. You can identify the URL required by navigating on your Salesforce account to Administer>Security Controls>Single Sign-On Settings. Click the name of your SAML Single Sign-On Settings. You are redirected to a page that displays the Salesforce Login URL (located under the Endpoints section of that page). |
Table 2: Add Google Workspace application
PROBLEM |
SOLUTION |
The administrator is not sure what URL to enter as the Single Sign-On URL to configure their G Suite account for Identity as a Service. |
Enter the URL of your Identity as a Service account, followed immediately by /api/saml/SAML2/SSO. An example would be https://example.us.trustedauth.com/api/saml/SAML2/SSO. |
Table 3: Logging in to Identity as a Service-configured applications
PROBLEM |
SOLUTION |
One of the applications configured for use on Identity as a Service cannot be logged in to by an administrator or user. |
Read through the steps outlined for configuring the specific application for Identity as a Service (see Add applications to Identity as a Service applications ). As you read through the steps, confirm the following: The Web application account is not currently logged in to by someone else. The Single Sign-On URL you have recorded for the applications' settings on Identity as a Service is correct. Where applicable, the Service Provider Initiated Request Binding setting within the user's application is set to HTTP Redirect and not HTTP POST. The error message "Invalid CORS request" may be displayed when a user attempts to authenticate to an application if the wrong Request Binding setting is selected. You have attached the SAML certificate as instructed in Integrate Salesforce with Identity as a Service or Integrate G Suite with Identity as a Service. All of the RADIUS settings information entered on Identity as a Service are correct. The SAML Identity Type the administrator selected, when Integrate Salesforce with Identity as a Service matches the type of attribute they selected (either email address or Federation ID) as that application's SAML NameID Attribute. The attribute that you selected for the user as the Federation ID Attribute contains a user name that is registered on the account of the application being accessed. The user attempting to access the application has been assigned to the appropriate group, and is not in violation of any resource rules associated with the application. No pop-up blockers are preventing the user from logging into the application from the Identity as a Service user portal. For additional assistance, contact support@entrust.com. |
Table 4: Delete an application
PROBLEM |
SOLUTION |
The application still appears to be configured after being deleted from Identity as a Service portal. |
Refresh your Web browser. Contact support@entrust.com if the problem persists. |
Table 5: Configuring Entrust Identity Desktop for Microsoft Windows with Identity as a Service
PROBLEM |
SOLUTION |
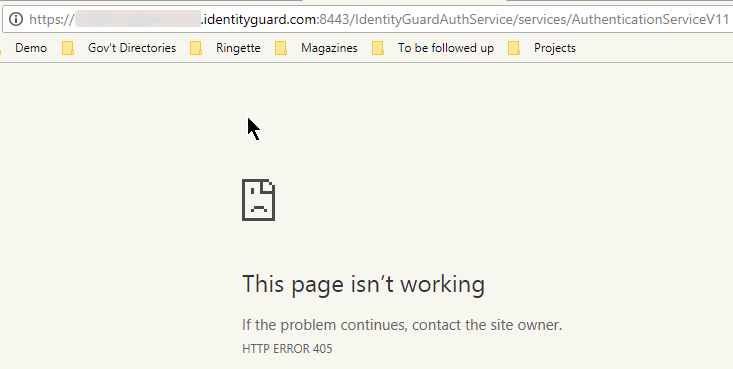
"405 Error" displayed on Web browser when validating connection between Entrust Identity for Microsoft Windows and Identity as a Service using a Web browser. Note: The connection is validated by entering the URL address of your Entrust Identity Desktop for Microsoft Windows account into a Web Browser.
|
This error message is expected. The Identity as a Service gateway responds by displaying a 405 error on an Internet Explorer, Chrome, or FireFox Web browser once a connection is established between Identity as a Service and Entrust Identity Desktop for Microsoft Windows. |
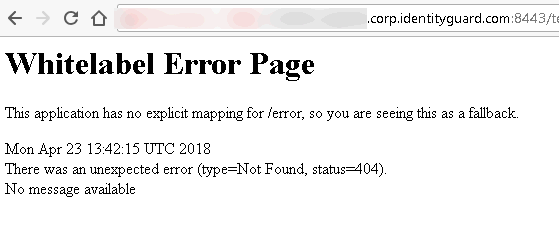
"White Label Error" displayed on Web browser when validating connection between Entrust Identity Enterprise for Microsoft Windows and Identity as a Service using a Web browser. Note: The connection is validated by entering the URL address of your Entrust Identity Desktop for Microsoft Windows account into a Web Browser.
|
The Entrust Identity Enterprise for Microsoft
Windows account URL is not recognized.
Confirm your Entrust Identity Enterprise for Microsoft Windows account URL Re-enter the account URL Contact support@entrust.com if the problem persists. |
Table 6: CORS log in error
PROBLEM |
SOLUTION |
During logging in the browser shows the following error: {"errorCode":"Invalid_cors_origin_in_request","errorMessage":"Invalid_request_origin.","parameters":null} and the origin header shows “Origin: null” in the request, which causes the error. |
Change the setting Referrer-Policy to strict-origin-when-cross-origin |
For additional assistance, please contact support@entrust.com.
 icon appears next to
the URL that you have entered.
icon appears next to
the URL that you have entered.