MacOS: Configure certificates and CAs
The Entrust Device Agent supports client authentication through a device certificate on both Windows and MacOS systems. The Entrust Device Agent receives a list of acceptable Certificate Authorities (CAs) from IDaaS, locates a local device certificate issued by one of these CAs, and forwards it to IDaaS to finalize the client authentication process.
On the IDaaS side, trusted CAs must be configured following the instructions outlined in Configure a Trusted CA.
Locally, certificates and CAs need to be configured.
The following is required to set up a valid device certificate to be used for IDaaS client authentication on Mac.
The device certificate needs to have one of the following purposes for Extended Key Usage (2.5.29.37)
Any Extended Key Usage (2.5.29.37.0)
Client Authentication (1.3.6.1.5.5.7.3.2)
The device certificate needs to have Digital Signature usage for Key Usage extension (2.5.29.15).
The issuer CA certificate of the device certificate needs to be present in a login keychain or system keychain.
The issuer CA needs to be in the trusted CAs list of IDaaS.
Private Key Access Prompt
The Mac Device Agent Service uses a custom clientauth executable for client authentication. In this process, the executable attempts to locate a device certificate and transmit it to the SSL server. Consequently, the ClientAuth executable requires access to the private key linked with the device certificate. Upon initial login attempt to IDaaS following installation, end users will see the following prompt:
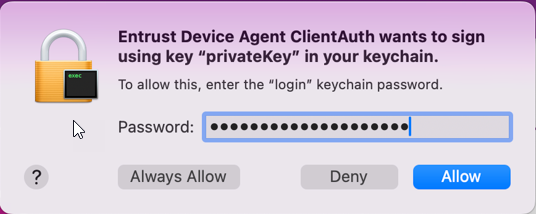
Users can prevent this prompt from reappearing by selecting Always Allow.